Abstract
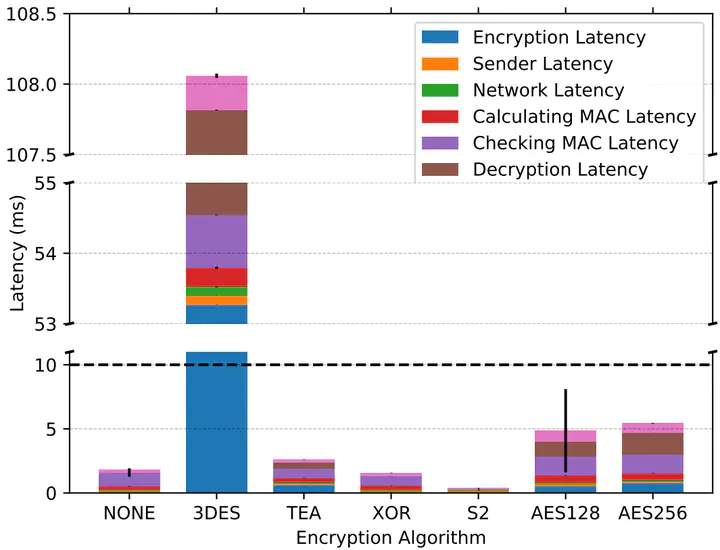
As automotive security concerns are rising, the Controller Area Network (CAN) — the de facto standard of in-vehicle communication protocol — has come under scrutiny due to its lack of encryption and authentication. Several vulnerabilities, such as eavesdropping, spoofing, and replay attacks, have shown that the current implementation needs to be extended. Both academic and commercial solutions for a Secure CAN (S-CAN) have been proposed, but OEMs have not yet integrated them into their products. The main reasons for this lack of adoption are their heavy use of limited computational resources in the vehicle, increased latency that can lead to missed deadlines for safety-critical messages, as well as insufficient space available in a CAN frame to include a Message Authentication Code (MAC). By making a trade-off between security and performance, we develop S2-CAN, which overcomes the aforementioned problems of S-CAN. We leverage protocol-specific properties of CAN instead of using cryptographic primitives and design a “sufficiently secure” alternative CAN with minimal overhead on resources and latency. We evaluate the security of S2-CAN in four real-world vehicles by an automated vehicular attack tool.We finally show that CAN security can be guaranteed by the correct choice of a design parameter while achieving acceptable performance.