MichiCAN: Spoofing and Denial-of-Service Protection using Integrated CAN Controllers
Jan 1, 2025· ,,,,,·
0 min read
,,,,,·
0 min read
Mert D. Pesé
Bulut Gozubuyuk
Eric Andrechek
Habeeb Olufowobi
Mohammad Hamad
Kang G Shin
Abstract
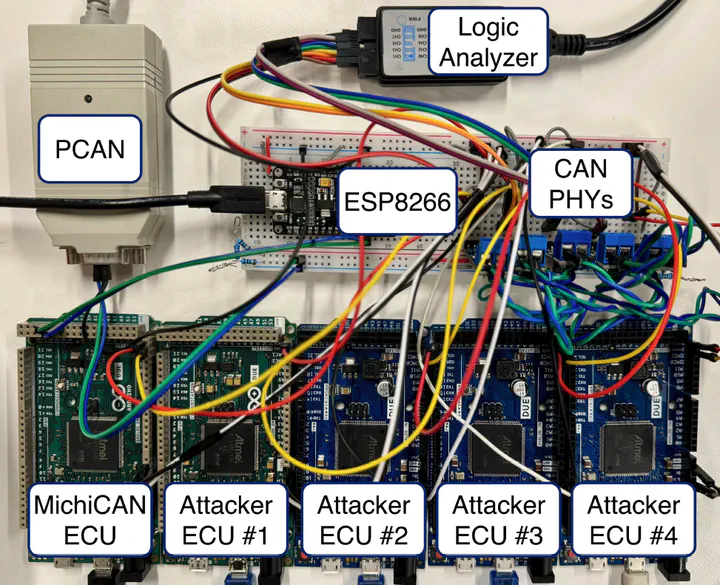
The Controller Area Network (CAN) has been the de facto in-vehicle network protocol since the 1980s, despite lacking essential security principles like authenticity, confidentiality, integrity, and availability. CAN is especially vulnerable to Denial-of-Service (DoS) attacks, threatening the availability of safety-critical functions. Existing countermeasures have seen limited adoption due to challenges in real-time detection, prevention, and high overhead on Electronic Control Units (ECUs). To address these issues, we propose MichiCAN, a distributed, backward-compatible, real-time defense against DoS and spoofing attacks. MichiCAN leverages integrated/on-chip CAN controllers in modern MCUs, enabling bit-level access to CAN messages. This allows MichiCAN to detect DoS attacks during the arbitration phase and neutralize them by bussing off the attacker ECU swiftly. Experiments on a CAN bus prototype and a real vehicle demonstrate MichiCAN’s effectiveness in enhancing automotive network security.
Type
Publication
55th Annual IEEE/IFIP International Conference on Dependable Systems and Networks