Abstract
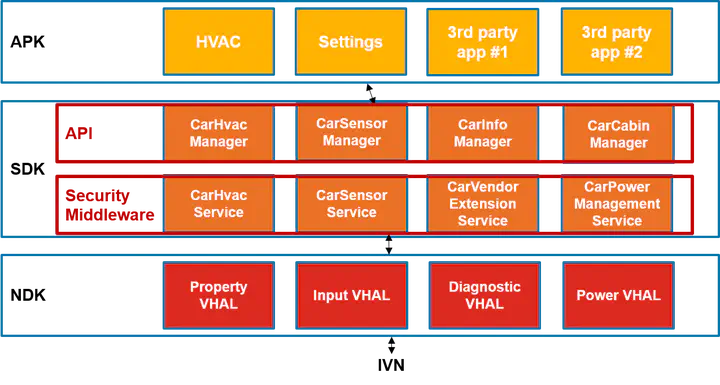
In-vehicle infotainment (IVI) platforms are getting increasingly connected. Besides OEM apps and services, the next generation of IVI platforms are expected to offer integration of third-party apps. Under this anticipated business model, vehicular sensor and event data can be collected and shared with selected third-party apps. To accommodate this trend, Google has been pushing towards standardization among proprietary IVI operating systems with their Android Automotive platform which runs natively on the vehicle’s IVI platform. Unlike Android Auto’s limited functionality of display-projecting certain smartphone apps to the IVI screen, Android Automotive will have access to the in-vehicle network (IVN), and will be able to read and share various vehicular sensor data with third-party apps. This increased connectivity opens new business opportunities for both the car manufacturer as well as third-party businesses, but also introduces a new attack surface on the vehicle. Therefore, Android Automotive must have a secure system architecture to prevent any potential attacks that might compromise the security and privacy of the vehicle and the driver. In particular, malicious third-party entities could remotely compromise a vehicle’s functionalities and impact the vehicle safety, causing financial and operational damage to the vehicle, as well as compromise the driver’s privacy and safety. This paper presents an Android Automotive system architecture and provides guidelines for conducting a high-level security analysis. It also describes what countermeasures have already been taken by Google to prevent potential attacks, and discusses what still needs to be done in order to offer a secure and privacy-preserving Android experience for next-generation IVI platforms.